Was the Nobaks washing coding in Iran before the penetration of $ 90 million?
The main headlines of $ 90 million have occupied the largest encryption exchange in Iran, Nobetix, the headlines of the international newspapers. But the newly -appeared Blockchain data shows the latter detecting something larger.
The forensic report by Blockchain Intelligence Global Ledger found that months before the June 18 attack, Nobitex systematically transferred users’ money using technologies usually related to money laundering.
Was the stock market washing user boxes before penetration?
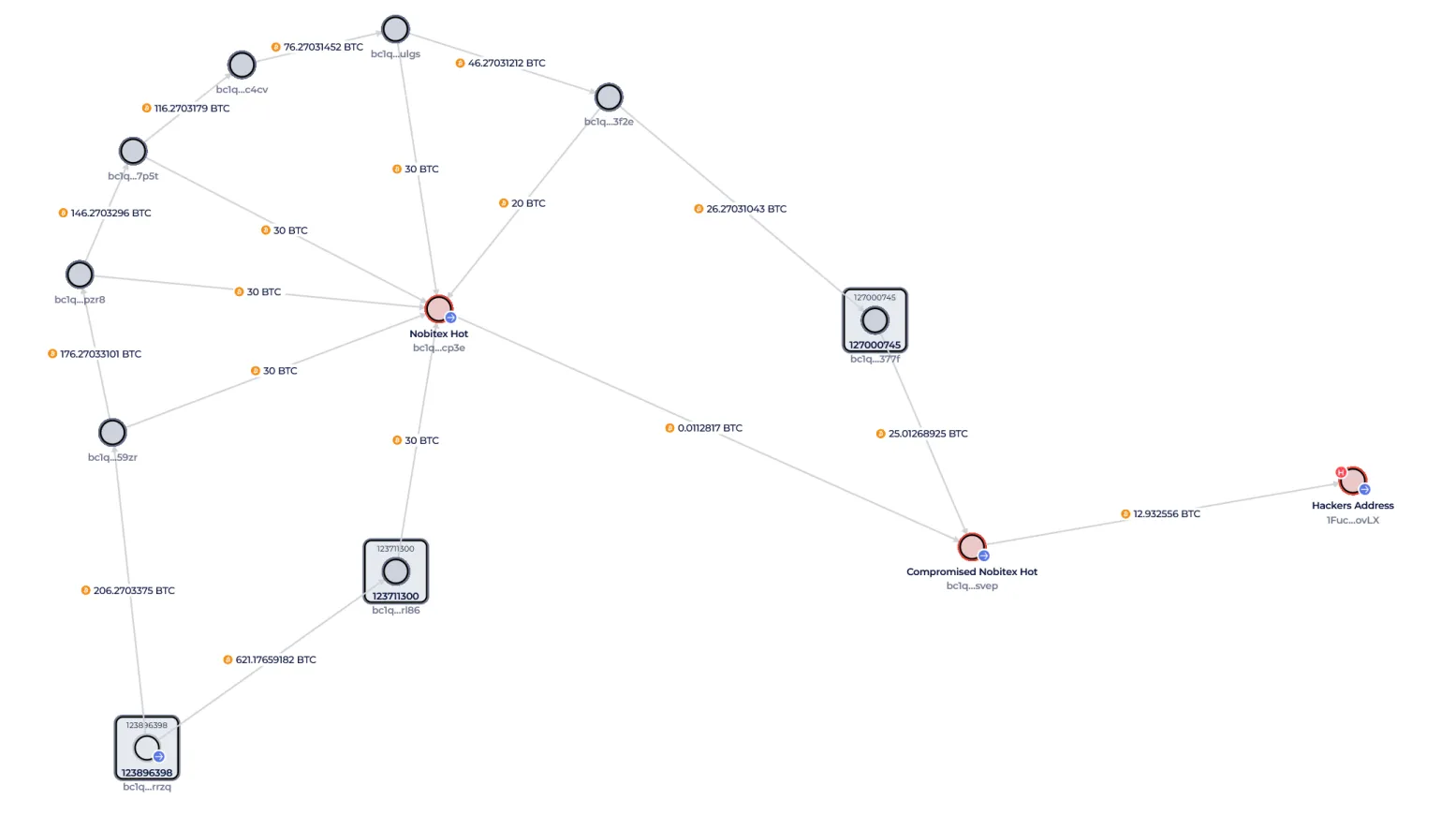
Data appears on the series that nobitex used a method called peelchaning. This is when large amounts of bitcoin are divided into smaller parts and directed through short -term portfolios.
This technique makes the money tracking difficult and is often used to hide the assets of money. In the Nobitex case, analysts found a pattern of BTC rotated in fixed pieces of 30-COIN.
Global Ledger also found that nobitex used deposit and segmental deals-behavior known as chip transactions. This one -use BTC is treated in new portfolios and hides liquidity paths.
The “rescue portfolio” was not new
After the penetration, Nobitex claimed that he transferred the remaining money as safety measure. The activity on the chain showed the process of scanning 1,801 BTC (at a value of about $ 187.5 million) in a newly created wallet.
But this wallet was not new. Track Blockchain data Historical use again to October 2024. The wallet has long collected the cut money.
This multiple “rescue portfolio” has received 20-30 BTC transfers that followed the same washing patterns, even before the hacking occurred.
Post -fishing activity shows continuous control
Hours after the violation, NoBitex moved the money from its exposed hot portfolio to another inner address. This full balance scanning indicated operating control.
On June 19, investigators noted that 1783 BTC was transferred to a new destination portfolio. This general claim of Nobitex is identical to securing its assets – but now with an additional context.
The flows indicate that instead of responding to the penetration, Nobitex was simply followed the playing book that was already exist to money laundering.
The pro -Israel piracy group Gonjshke Darande has published files that showcase the Nobitex interior portfolio.
The penetration may have shocked users, but Blockchain data shows this NOBITEX was already transporting money in this way for several months.
The old portfolio associated with the exchange regularly sent Bitcoin to a new governor. From there, the money was divided into smaller amounts and has moved again and again – often in cutting 20 or 30 BTC.
This method makes it difficult to follow the place where the money ends. It is similar to how some people hide their paths when transferring money by encryption.
The important thing is that this was not anything that NoBitex started after hacking. They were doing it a long time ago, and they continued to do so yet –Almost like a standard procedure.
One wallet in particular –BC1Q … RRZQ– Review over and over again. He has received many user deposits and it appears to be the starting point for many boxes that are difficult to track.
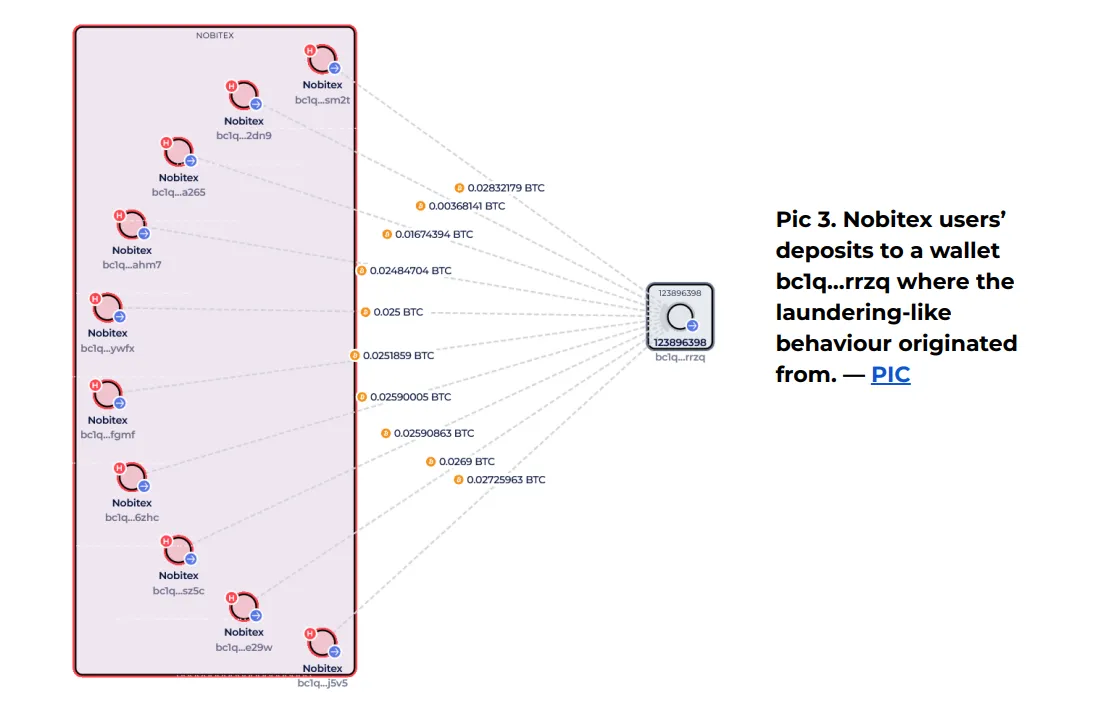
In short, the penetration did not change how it dealt with the money. Simply brought Continuing behind the scenes in the eye of the audience.
Disintegration
In adherence to the confidence project guidance, beincrypto is committed to unprepared and transparent reporting. This news article aims to provide accurate information in time. However, readers are advised to independently verify facts and consult with a professional before making any decisions based on this content. Please note that the terms, conditions, privacy policy have been updated and the evacuation of responsibility.




