EIP-7702 codes of Ethereum Pectra’s EIP-7702 takes advantage of
The recently introduced ETHEREMM feature, EIP-7702, is subject to scrutiny after Blockchain security researchers have discovered the abuse of Internet criminals. After the Pectra upgrade, many wallet providers began to integrate EIP-7702 features.
Wintermute analysts, the encryption trading company, indicated that the attackers used 97 % of the EIP-7702 wallet delegations to publish contracts designed to drain money from reassuring users.
EIP-7702 infiltrators from ETHEREUM are used to automate mass portfolio drainage
EIP-7702 Externally owned accounts (EOAS) is temporarily allowed to work as a conservative of the smart nodes. The upgrade provides features such as transactions renewal, spending boundaries, traffic key integration, and wallet recovery – all without changing portfolio addresses.
While these promotions aim to enhance the ability to use, harmful actors benefit from the standard to accelerate the fund extracts.
Instead of manually transferring ETH from each risk portfolio, attackers now allow the contracts that are automatically redirect to their own addresses.
“There is no doubt that the attackers are one of the first adopters of the new capabilities. 7702 was never supposed to be a silver bullet and have great use cases,” Rahul Romala, SAFE chief product official, He said.
Wintermute analysis shows that most of these wallet delegations indicate the identical code bases designed “ETH” from the governor at risk.
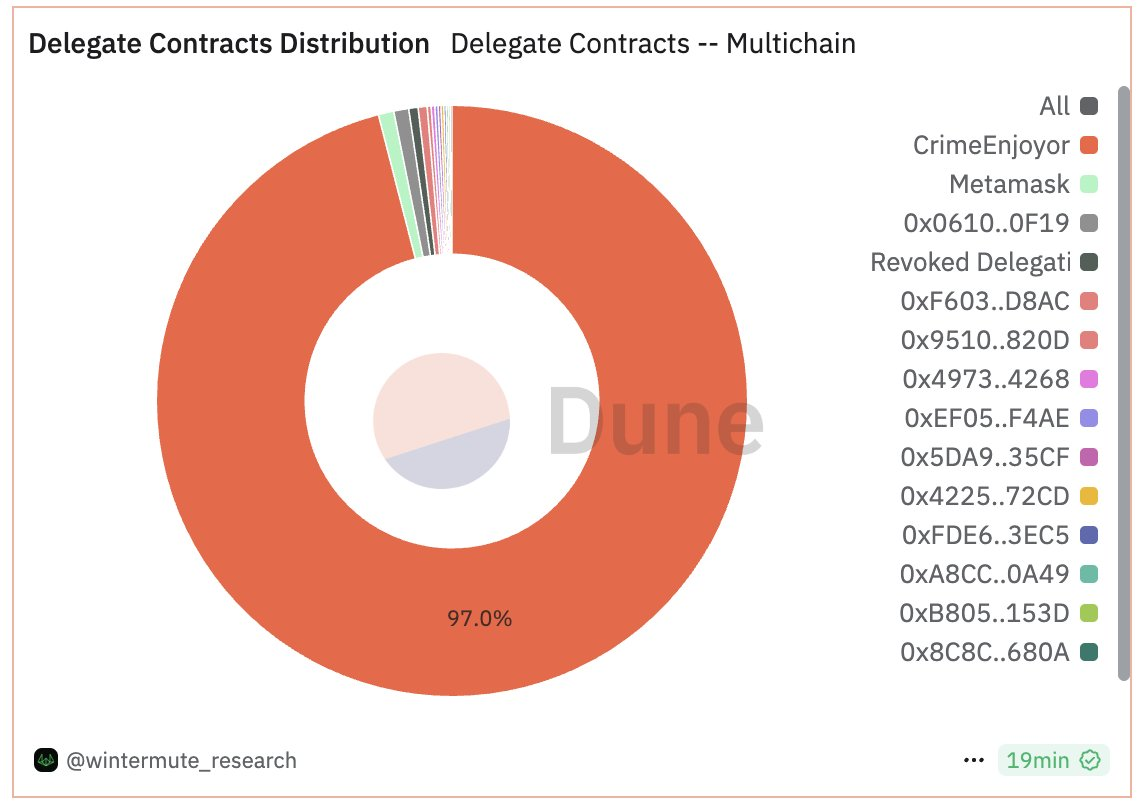
These churches automatically transfer any money received to attacking headlines controlled by the attacker. Of nearly 190,000 delegated contracts, more than 105,000 illegal contracts have been linked.
KOFFI, the chief data analyst at Base Network, explained that more than a million portfolios interacted with suspicious contracts last week.
He explained that the attackers did not use EIP-7702 to penetrate the governor, but to simplify the theft from the governor with special open keys already exposed
The analyst has strengthened that one of the prominent applications includes a reception function that leads to the transfer of ETH at the moment of funding of money in the wallet, which eliminates the need for manual withdrawal.
Yu Xian, founder of Blockchain SlowMist, confirmed that the perpetrators of the perpetrators are theft organizations, not the typical hunting operators. He pointed out that the capabilities of automation in the EIP-7702 make it especially attractive to the exploits on a large scale.
“The new EIP-7702 mechanism is used by the metal currency theft groups (not hunting groups) to automatically transfer money from the portfolio addresses using the leaked key/Mnemonics keys”, ” I mentioned.
Despite the size of the operation, there are no confirmed profits yet.
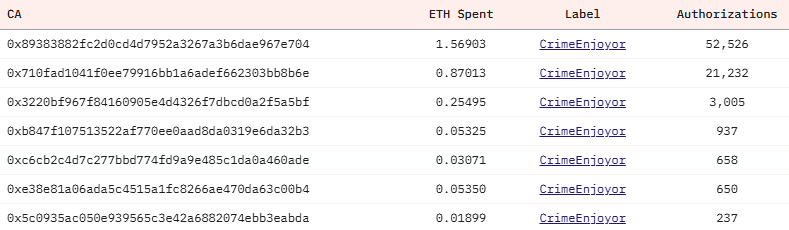
Researcher at Wintermute male The attackers spent about 2.88 ETH, more than 79,000 titles. One address alone implemented approximately 52,000 charges, yet the target address did not receive any money.
Disintegration
In adherence to the confidence project guidance, beincrypto is committed to unprepared and transparent reporting. This news article aims to provide accurate information in time. However, readers are advised to independently verify facts and consult with a professional before making any decisions based on this content. Please note that the terms, conditions, privacy policy have been updated and the evacuation of responsibility.




