Trezour the deception attack violated emails for the support office
Earlier today, Trezor warned users of the hunting fraud coming from its auxiliary line. HTML’s exploitation of criminals allowed the release of Trezor support messages to include false warnings and bonds to their risk.
It is not currently clear whether anyone has already occurred in this fraud, but it may be a small silver lining. This attack could have been carried out using data from previous violations, making the perpetrators difficult to follow.
The fraudsters target the users of the hardware portfolio
Trezor, a leading brand in the hardware portfolio, has been targeted in many breaches, exploits and violations over the past few years. The encryption industry faces a wave of attacks at the present time, and the wallet appears to be threatened again.
Earlier today, Trezor warned its customers of a possible fraud in the form of emails support:
Trezor’s client attack was somewhat elegant. The company’s communications did not provide a lot of information about the details, claiming only that “there was no email breach” and that the situation was under control.
However, the monitoring of cyberspace It was identified A possible threat yesterday, and Trezor Trembling This is the perpetrator.
The infiltrators announced a breach of Trezor safety on the dark web, as they redirect technical details to those who would pay $ 10,000. This violation of the HTML chain to edit emails sent from the Trezor Support Office.
Elderly individuals can ask “help” from this email, and fill in potential victim’s contact information instead of their own.
The request will then contain the HTML icon, which adjusts the automatic responses of Trezor to include an attempt to hunt. The modified email will come out, apparently from a project source.
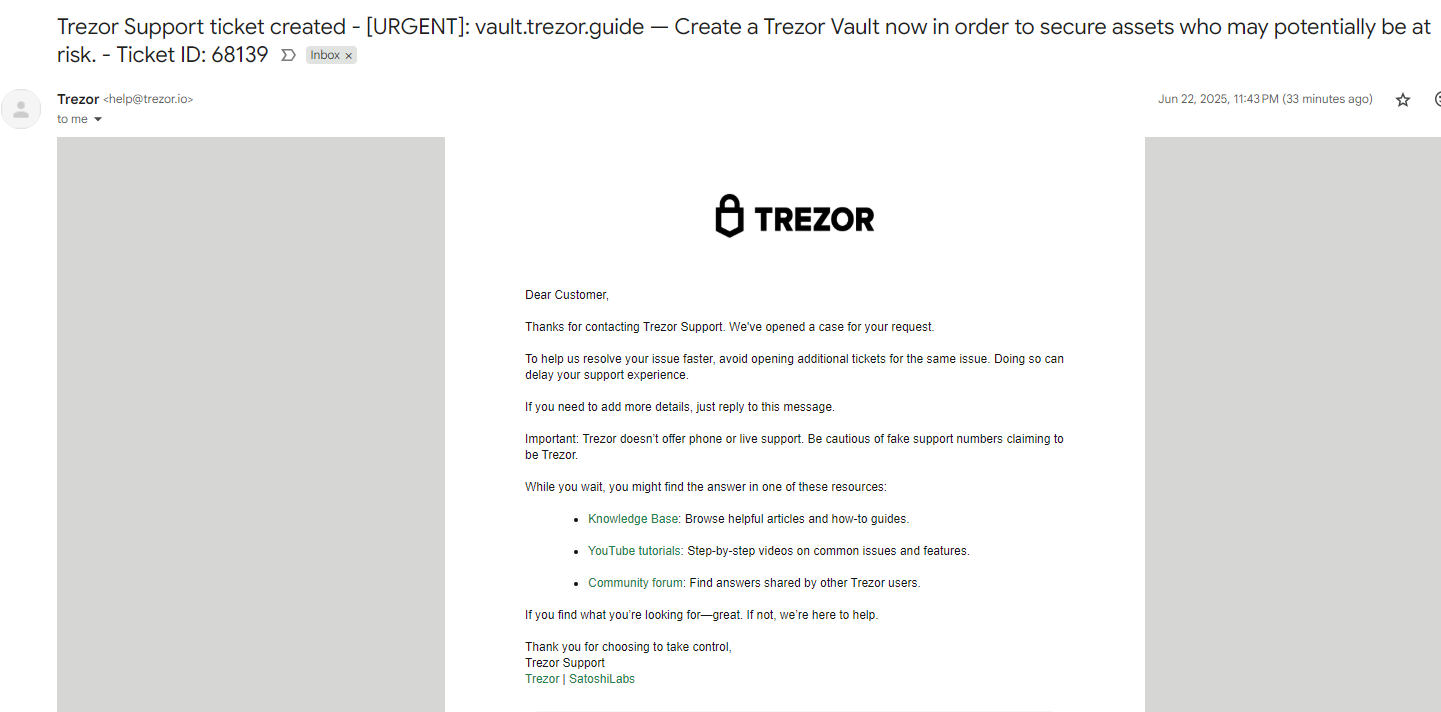
From the user’s point of view, the Trezor aid office will send an unexpected email. Trezor’s email body will discuss a fake support “, while the topic will have an attempt to hunt.
This undoubtedly is that web2 fraud efforts can withhold device customers in losing everything.
Last year, Trezor warned its customers that 66,000 users contacted its support line may have been at risk. In other words, contact information for these people may be available for purchase on seedien sites.
The infiltrator will need to purchase the data of the Trezor user and HTML code to exploit the support emails, and this may lead to a large -scale fishing.
In other words, there are no clear threads on the perpetrator of cabinet crime because they did not violate Trezor themselves. Other infiltrators stole user data and found HTML breach, both of whom were offered for sale.
We hope that investigators can track these fake support requests, but it is not clear whether this will work.
Over the past few months, fraud in social engineering with low skill has proven successful in penetrating encryption security. Trezor portfolios are very safe, but the hunting attack can attract users to a transgression protection.
In this environment, everyone needs to stay on alert to prevent fraud.
Disintegration
In adherence to the confidence project guidance, beincrypto is committed to unprepared and transparent reporting. This news article aims to provide accurate information in time. However, readers are advised to independently verify facts and consult with a professional before making any decisions based on this content. Please note that the terms, conditions, privacy policy have been updated and the evacuation of responsibility.




